
Thoughts on what is next for æternity blockchain and beyond.
About two weeks ago we became victim of a bug of an Ethereum “smart contract” written by one of the most reputable companies in the Ethereum space. The problem was not the wallet itself, nor the private keys, but the smart contract, which was supposedly an especially secure multi-signature contract used by many projects in the space. A multi-signature contract is a contract where several parties need to sign to create a transaction of ETH to another Ethereum account.
Some might feel sympathy for the attacker. He/she showed again, that it is very difficult to write a secure smart contract on Ethereum — without a team of researchers, formal verification experts and a test-framework behind. In this particular hack, the attacker was able to simply exchange the owners of the multisig contract, by sending a transaction on the public Ethereum network, which made himself the owner. As a second step, he was able to transfer all the ETH out to his account.
“The Lord giveth, and the Lord taketh away.”
Because of this incident we lost control of over 82k ETH (worth about 18m CHF or USD at the time). We at Aeternity had to discuss again about how to proceed and also about the maturity of the Ethereum ecosystem. This would have never happened with Bitcoin, we figured, where there has not been a single incident where a multisig-contract got hacked.
Further, remaining questions are whether the cause of the problem is Solidity (as a language), Ethereum (as a platform) or the negligence of the developer of the multisig wallet contract that was hacked, or a simply a human error.
No doubt, æternity suffers from this incident. But we don’t give up and believe that in the future blockchain technology and smart contracts will be one of the biggest enablers in this world, especially for the developing regions. We proceed to implement our vision of a more scalable, more user-friendly, more secure, and more decentralized blockchain platform.
Since inception, we at æternity blockchain believe that smart contracts should be done another way. The idea that every JavaScript developer should write a financial application is possibly one of the worst in this century. Contracts calling contracts calling contracts are hard to verify — without the right tools at least. At æternity, we currently use a dialect of Forth (like Bitcoin script) and a dialect of Lisp to write smart contracts in, which are in from each other isolated state channels. We will further explore methods of writing even more secure smart contracts and will put more efforts into creating the right tools to verify contracts.
New Bounties by æternity
To engage further with the community, we are announcing following bounties:
1. Return-the-ETH-bounty (10% of returned ETH)
Anyone, either the black hat or a white hat guy/girl/group, who returns us the ETH originating from our attacked contract address to the below address, can keep 10% of the ETH. This bounty is potentially worth several millions and is valid for everybody who returns the ETH back to the below address. We are working with the local authorities and newly on-boarded professionals to assist us.
Dear exchanges and dear crypto-crowd, please help us get the ETH back — you will be highly rewarded. As an immediate step, please blacklist the root address and all child-addresses of the attacker.
Dear Multisig Contract attacker, if you are reading this, please know that we are serious about building a better, more secure smart contract platform. A truly decentralized one and one which scales. We are asking you kindly to return the ETH you took from the æternity project to the below address, and we will stop any further legal actions.
https://etherscan.io/address/0x541dE0Cd1F7eef8bdae28FBB146298EEfa993A25
Feel also free to send messages to this address.
Timeframe: Unlimited.
2. Taint Analysis Tool (4 ETH)
Whoever writes a script (nodeJS preferred), which is capable to track ETH movements on the Ethereum blockchain, will receive 4 ETH. The script should take one root address as an input, request data from Etherscan, and then follow the transactions to the next addresses, where the ETH get sent to. It should auto-update. It should have a JSON API and an simple HTML interface, so that exchange and other people can easily track the movements of ETH. Open Source license, preferably MIT. Development should happen in public.
This tool will also help to track down the recent phishing attacks.
Bonus (2 ETH): get etherscan.io to have this taint analysis implemented into their service, in a publicly accessible way.
Bonus (1 ETH): make it possible that community members comment on the addresses via a third party identity provider.
Good things about such a attack: The attacker will not be able to spend such big amounts. Fiat-gateways are monitored. Ethereum transactions are fully public and can be tracked easily. To a certain amount laundering is possible though. But humans make errors all the time.
For this reason, it is important, that all of you, dear members of the crypto community, try to help to annotate the transactions of the ETH which got hacked. If we work together we can catch not only the Multisig Contract attacker, but also the group behind the recent phishing attacks and make the crypto-sphere a generally more secure place.
Timeframe: 1 week (extension possible).
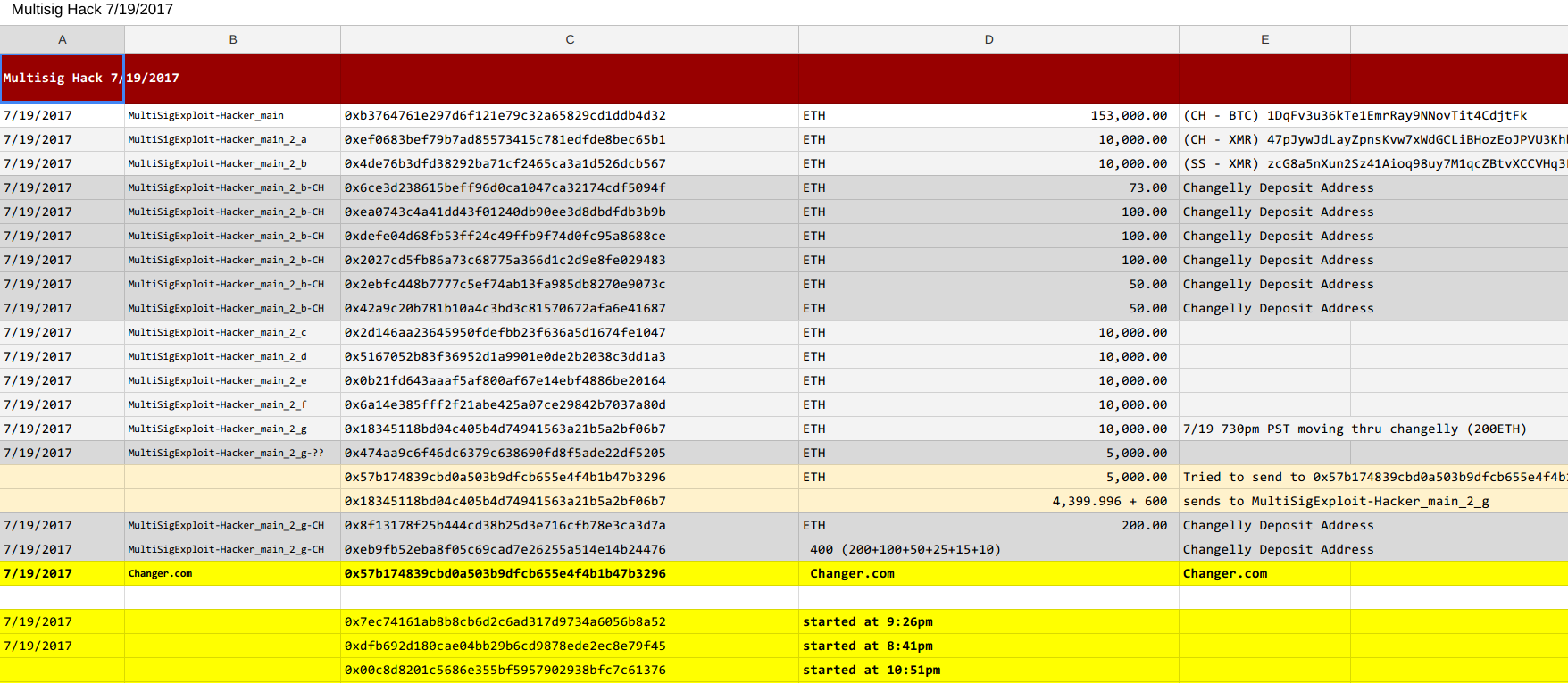
3. Attack analysis on public testnet blockchains (5 ETH)
The attacker might have not been careful when he did his first attempts to hack the multisig wallet contracts. He/she might have done some attempts on public testnet blockchains where he first deployed a multisig contract and then tried to attack it. Goal for this task is to write a script, which hooks into the currently available public ETH-style blockchains and finds the attack pattern. The person who gets the bounty should deliver himself an analysis of all the available ETH testnet blockchains as well as the ETC blockchain. This should happen as a public blog post. Additionally, the origin of the ETH, which were used for the attack, should be traced back.
Timeframe: 1 week (extension possible).
Path Forward for æternity’s AE Token Contract
Allocation of the æternity Blockchain AE Tokens
The AE tokens will be initially allocated exactly as announced in earlier official statements. æternity will not have more, nor less AE tokens because of the attack.
Launch of the æternity AE token contract on Ethereum
The recent hack had caused us to be very busy and made us consider restructuring the token distribution method, e.g. via using the ColoredCoins protocol on BTC or LTC. We will continue with the creation of a very simple ERC20 token contract on Ethereum. We expect the launch of the AE token contract during August. However, this did not halt our progress with the platform as can be seen in our GitHub and development updates.
We understand our community and that it takes more time than anticipated, but be patient, we are working very hard to assure the success of æternity platform and the delivery of it in the most efficient way.
Please subscribe to our email newsletter or check our blog, if you want to stay updated on the exact date of the AE token launch.
Read more about the Hack
https://etherscan.io/address/0x541dE0Cd1F7eef8bdae28FBB146298EEfa993A25https://etherscan.io/address/0x541dE0Cd1F7eef8bdae28FBB146298EEfa993A25https://etherscan.io/address/0x541dE0Cd1F7eef8bdae28FBB146298EEfa993A25https://etherscan.io/address/0x541dE0Cd1F7eef8bdae28FBB146298EEfa993A25https://etherscan.io/address/0x541dE0Cd1F7eef8bdae28FBB146298EEfa993A25https://etherscan.io/address/0x541dE0Cd1F7eef8bdae28FBB146298EEfa993A25
Bugs have happened also before the æra of the blockchain…
https://etherscan.io/address/0x541dE0Cd1F7eef8bdae28FBB146298EEfa993A25https://etherscan.io/address/0x541dE0Cd1F7eef8bdae28FBB146298EEfa993A25
If you have anything to comment, please do so here on Medium. Thank you!
…and let the Lord giveth back.

Leave a Reply